What’s new in the NIST CSF Framework 2.0
Significant updates to the widely used cybersecurity framework

Written by:

TL;DR
In this blog post, we’ll go through some of the most important changes to the new version of the National Institute of Standards and Technology's (NIST) Cybersecurity Framework (CSF). This includes:
- Broadened scope
- Integration with other frameworks
- Enhanced implementation guidance
- Larger emphasis on cybersecurity governance
- More emphasis on continuous improvement
NIST recently made the CSF 2.0 draft available for the public, and it’s clear to say that the new version intends to make sure CSF remains relevant in the future while still staying true to the original goals and objectives of the CSF.
CSF 2.0 seems to be emphasising the importance of top-down governance and the integration of cybersecurity into overall business strategy. This is apparent from one of the most major changes from version 1.1; the new GOVERN function. This function emphasises that cybersecurity isn't just about IT; it's an integral part of an organisation's governance and strategic planning.
The NIST Cybersecurity Framework 2.0: Key Changes from Version 1.1 to 2.0
NIST released the Public Draft of the NIST CSF Framework 2.0 on August 8th, 2023. The framework, since its initial publication in 2014, has been widely adopted to mitigate cybersecurity risks. While CSF 1.1 remains effective, there's a consensus that the framework needs to be updated to address the ever changing cybersecurity landscape.
The key changes in the new version include:
Broadened Scope of the Framework
The title of the framework has been changed from the original "Framework for Improving Critical Infrastructure Cybersecurity" to the more commonly used "Cybersecurity Framework". The scope has been expanded to cater to all organisations on a global scale, moving away from a focus solely on U.S. critical infrastructure.
Integration with Other Frameworks
NIST has incorporated references to other recent resources, including the NIST Privacy Framework, NICE Workforce Framework for Cybersecurity, Secure Software Development Framework, and more.
Enhanced Implementation Guidance
The draft introduces Implementation Examples to provide action-oriented processes to achieve CSF Subcategories.
Emphasis on Cybersecurity Governance
A new function, "GOVERN", has been added to cover various aspects like organisational context, risk management strategy, cybersecurity supply chain risk management, and more. There's also guidance on integrating the framework with the NIST Privacy Framework and with enterprise risk management.
Emphasis on continuous improvement
Information on cybersecurity assessments has been updated with references to NIST SP 800-55. The importance of continuous improvement is emphasised, with a new Improvement Category in the IDENTIFY Function.
Feedback and Further Development
NIST is actively seeking feedback on this draft and the related Implementation Examples draft. All feedback can be submitted to [email protected] by November 4th, 2023. Feedback received will be discussed and the final CSF 2.0 is expected to be published in early 2024.
The NIST Cybersecurity Framework 2.0: Understanding the Framework Core
The NIST Cybersecurity Framework 2.0 provides a structured approach to managing cybersecurity risks. One of the core components of the framework is the "Framework Core," which is a set of desired cybersecurity outcomes organised into Functions, Categories, and Subcategories. Here's a brief overview:
The Framework Core provides a set of activities, outcomes, and references that detail an approach to cybersecurity risks. It is designed to be intuitive and to act as a translation layer to enable communication between different teams within an organisation, from the executive level to the implementation and operations level.
Functions
These are the primary high-level activities that form the backbone of the Framework Core. They help organisations manage and reduce cybersecurity risks in a coordinated manner.
Categories
Within each function, there are categories that are specific outcomes of technical and/or management activities.
Subcategories
These further divide each category into specific outcomes of activities.
The Framework Core also provides two types of additional resources with information to help achieve the outcomes described in the Core’s Subcategories.
- Informative references help organisations better understand the outcomes outlined in the framework. They may include standards, guidelines, best practices, and other relevant documents that can provide further insights into specific areas of cybersecurity. In some cases, the Informative Reference is more specific than a Subcategory. In that case, more than one control would be used to achieve the outcome described in one Subcategory. In other cases, organisations may leverage higher-level policies or requirements that address one or more Subcategories. Informative References can also be sector or technology specific.
- Implementation Examples provide notional examples of concise, action-oriented steps to help achieve the outcomes of the Subcategories. The examples are not a comprehensive list of all actions that could be taken by an organisation to achieve an outcome, nor do they represent a baseline of required actions to address cybersecurity risk.
The NIST Cybersecurity Framework 2.0: The CSF 2.0 Core
The new version has 6 functions, 22 categories and 106 subcategories while the former had 5 functions, 23 categories and 108 subcategories.
The table below shows the outcomes of the functions and categories as stated in the public draft:
| Function | Category |
| GOVERN (GV) - Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy |
Organizational Context (GV.OC): The circumstances — mission, stakeholder expectations, and legal, regulatory, and contractual requirements — surrounding the organization’s cybersecurity risk management decisions are understood Risk Management Strategy (GV.RM): The organization’s priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions Cybersecurity Supply Chain Risk Management (GV.SC): Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders Authorities (GV.RR): Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated Policies, Processes, and Procedures (GV.PO): Organizational cybersecurity policies, processes, and procedures are established, communicated, and enforced Oversight (GV.OV): Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy |
| IDENTIFY (ID) – Help determine the current cybersecurity risk to the organization |
Asset Management (ID.AM): Assets (e.g., data, hardware software, systems, facilities, services, people) that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization’s risk strategy Risk Assessment (ID.RA): The organization understands the cybersecurity risk to the organization, assets, and individuals. Improvement (ID.IM): Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all Framework Functions |
| PROTECT (PR) – Use safeguards to prevent or reduce cybersecurity risk |
Identity Management, Authentication, and Access Control (PR.AA): Access to physical and logical assets is limited to authorized users, services, and hardware, and is managed commensurate with the assessed risk of unauthorized access Awareness and Training (PR.AT): The organization’s personnel are provided cybersecurity awareness and training so they can perform their cybersecurity-related tasks Data Security (PR.DS): Data is managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information Platform Security (PR.PS): The hardware, software (e.g., firmware, operating systems, applications), and services of physical and virtual platforms are managed consistent with the organization’s risk strategy to protect their confidentiality, integrity, and availability Technology Infrastructure Resilience (PR.IR): Security architectures are managed with the organization’s risk strategy to protect asset confidentiality, integrity, and availability, and organizational resilience |
| DETECT (DE) – Find and analyze possible cybersecurity attacks and compromises |
Continuous Monitoring (DE.CM): Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events Adverse Event Analysis (DE.AE): Anomalies, indicators of compromise, and other potentially adverse events are analyzed to characterize the events and detect cybersecurity incidents |
| RESPOND (RS) – Take action regarding a detected cybersecurity incident |
Incident Management (RS.MA): Responses to detected cybersecurity incidents are managed Incident Analysis (RS.AN): Investigation is conducted to ensure effective response and support forensics and recovery activities Incident Response Reporting and Communication (RS.CO): Response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies Incident Mitigation (RS.MI): Activities are performed to prevent expansion of an event and mitigate its effects |
| RECOVER (RC) – Restore assets and operations that were impacted by a cybersecurity incident |
Incident Recovery Plan Execution (RC.RP): Restoration activities are performed to ensure operational availability of systems and services affected by cybersecurity incidents Incident Recovery Communication (RC.CO): Restoration activities are coordinated with internal and external parties |
Let’s dive-in to what it each of these functions mean:
GOVERN (GV): By introducing this function, NIST acknowledges the need for a foundational layer that goes beyond mere technical and operational considerations. Establishing and overseeing a cybersecurity strategy that aligns with the organisation's broader mission and risk appetite is crucial. This function emphasises that cybersecurity isn't just about IT; it's an integral part of an organisation's governance and strategic planning.
IDENTIFY (ID): While the essence of this function remains largely unchanged from the original CSF, the split with the GOVERN function enhances its significance. By linking identification of risks with the broader organisational mission defined under GOVERN, it ensures that risk management is contextual and tailored to the organisation.
PROTECT (PR): By implementing the necessary safeguards, an organisation can either prevent or reduce the impact of threats. The scope covers several layers, from user awareness training to the physical and virtual infrastructure resilience.
DETECT (DE): The faster an organisation can detect a threat, the quicker it can respond and minimise damage. With an ever-evolving threat landscape, having robust detection mechanisms can make the difference between a minor incident and a major breach.
RESPOND (RS): It's not always about prevention. Sometimes breaches happen, and when they do, the response can determine the overall impact. A swift, well-coordinated response can not only contain the damage but also preserve trust and reputation.
RECOVER (RC): After addressing a cybersecurity event, getting back to "business as usual" is vital. This function ensures that processes are in place to restore impacted assets and operations quickly and efficiently.
Let further break-down each function into their categories:
GOVERN (GV) Categories Overview
Organisational Context (GV.OC): Understanding the broader circumstances, including stakeholder expectations and legal requirements, to tailor cybersecurity practices to an organisation's unique needs ensures alignment of cybersecurity measures with the organisation's mission and objectives.
Risk Management Strategy (GV.RM): Establishment and monitoring of the organisation’s cybersecurity risk management strategy in alignment with its broader mission ensures that every member of the organisation is aware of the risk parameters and can make decisions aligned with the broader risk management strategy.
Cybersecurity Supply Chain Risk Management (GV.SC): Understanding and managing risks related to the supply chain, which can introduce vulnerabilities, emphasises the need for a systematic approach to manage supply chain risks and ensure third parties maintain adequate cybersecurity standards.
Roles, Responsibilities, and Authorities (GV.RR): Clear definition of cybersecurity roles and responsibilities for accountability and efficient incident response ensures every team member is aware of their duties and knows the appropriate contacts in specific scenarios.
Policies, Processes, and Procedures (GV.PO): Developing and maintaining clear policies, processes, and procedures for consistent and effective cybersecurity ensures formalised cybersecurity practices that allow for regular reviews and updates as threats and technologies evolve.
Oversight (GV.OV): Ensuring that the cybersecurity strategy is continuously reviewed, updated, and overseen to remain relevant and effective maintains a feedback loop for refining strategies and rectifying any shortcomings in the current approach.
IDENTIFY (ID) Categories Overview
Asset Management (ID.AM): Understanding and managing assets crucial to the organisation's business objectives ensures prioritisation of cybersecurity measures based on the significance of assets in line with the organisation's risk strategy.
Risk Assessment (ID.RA): Comprehensive understanding of the cybersecurity risk to the organisation, its assets, and individuals provides a foundation for informed decision-making and prioritisation of cybersecurity efforts.
Improvement (ID.IM): Identifying enhancements to the organisation's cybersecurity risk management processes and activities ensures continuous refinement and adaptation of cybersecurity measures across all framework Functions.
PROTECT (PR) Categories Overview
Identity Management, Authentication, and Access Control (PR.AA): Limiting access to assets based on authorisation and assessed risk safeguards assets against unauthorised access, ensuring data integrity and confidentiality.
Awareness and Training (PR.AT): Providing cybersecurity awareness and training to personnel equips staff with the knowledge and skills to perform cybersecurity-related tasks effectively.
Data Security (PR.DS): Managing data in alignment with the organisation's risk strategy protects the confidentiality, integrity, and availability of information.
Platform Security (PR.PS): Management of hardware, software, and services of platforms ensures the security of platforms, safeguarding against potential vulnerabilities.
Technology Infrastructure Resilience (PR.IR): Management of security architectures to protect assets and ensure organisational resilience ensures the continuous availability and integrity of assets, even in adverse situations.
DETECT (DE) Categories Overview
Continuous Monitoring (DE.CM): Monitoring of assets to detect potential cybersecurity threats enables timely identification and mitigation of cybersecurity threats, reducing potential damage.
Adverse Event Analysis (DE.AE): Analysis of anomalies and potential threats to detect cybersecurity incidents provides insights into the nature and severity of threats, guiding response measures.
RESPOND (RS) Categories Overview
Incident Management (RS.MA): Management of responses to detected cybersecurity incidents ensures a coordinated and effective response to threats, minimising potential damage.
Incident Analysis (RS.AN): Investigation of incidents to guide response and recovery efforts provides insights into the cause and impact of incidents, informing mitigation strategies.
Incident Response Reporting and Communication (RS.CO): Coordination of response activities with stakeholders ensures a unified response and compliance with legal and regulatory requirements.
Incident Mitigation (RS.MI): Activities to prevent the escalation of incidents and mitigate their effects reduce the impact of incidents, safeguarding assets and operations.
RECOVER (RC) Categories Overview
Incident Recovery Plan Execution (RC.RP): Restoration activities post cybersecurity incidents ensure timely recovery of operations, minimising downtime and associated costs.
Incident Recovery Communication (RC.CO): Coordination of recovery activities with internal and external parties ensures a unified recovery process and keeps stakeholders informed.
The NIST Cybersecurity Framework 2.0: the two frameworks visualised
Let’s take a look at the relationship between the two framework versions visualised by the mnemonic Enterprise Security Architecture tool. The diagrams below show the differences between the 1.1 and 2.0 versions of the framework collapsed at the category level.
The most obvious change is the new GOVERN function built from several categories and subcategories in the 1.1 version of the Identify function:
Click image to view details
Moving to the IDENTIFY function, the new category Improvement (ID.IM) consolidates the separated Improvements categories in RESPOND and RECOVER functions in the former version. Another notable change in this function is how Asset Management (ID.AM) consolidates asset management practices from multiple PROTECT subcategories.
Click image to view details
In the PROTECT function Identity Management, Authentication, and Access Control (PR.AA) changes name from PR.AC and merges identity and access control practices into access permissions, entitlements, and authorisations. The former version categories Information Protection Processes and Procedures (PR.IP), Protective Technology (PR.PT), Detection Processes (DE.DP) are moved to several categories in different functions in the new version.
Click image to view details
In the DETECT function; integrity checking, formerly in PR.DS, are now unified in the Continuous Monitoring category (DE.CM). At the same time, Detection Processes (DS) is dropped and moved to other categories and functions.
Click image to view details
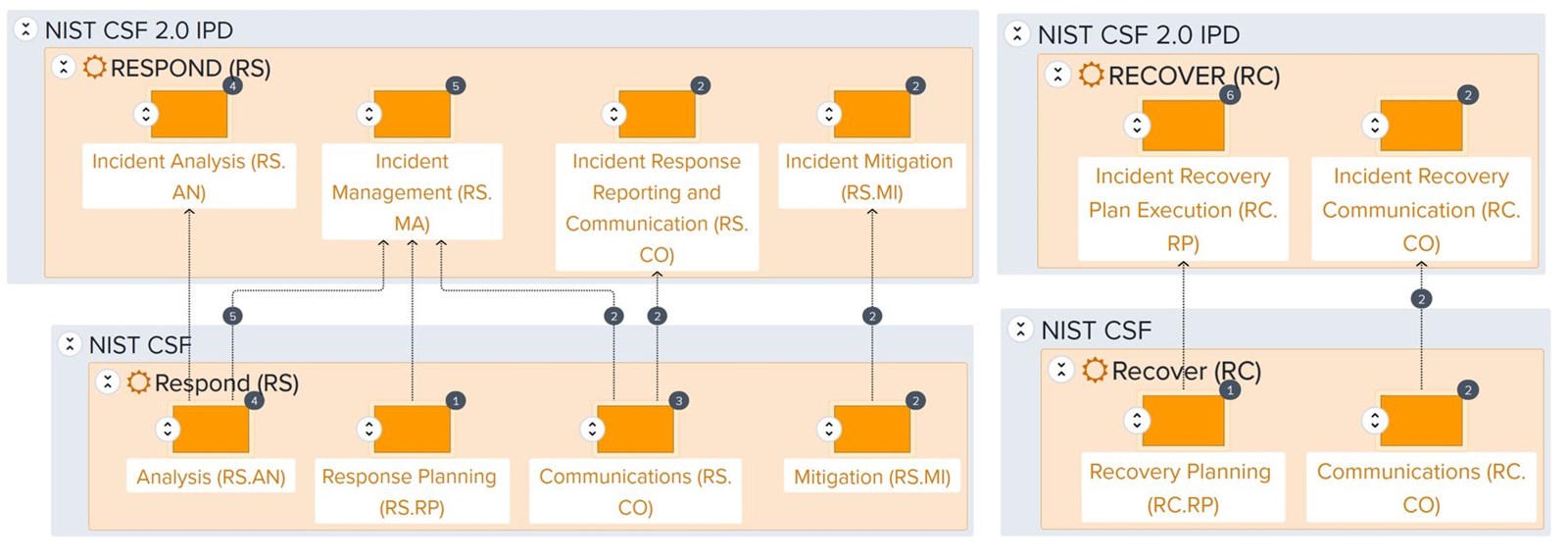
Finally, in the RESPOND and RECOVER functions, in the addition to the previously mentioned move of the separate improvement categories to its own Improvement (ID.IM) category in the IDENTIFY function, several merges and new subcategories are now present.
Click image to view details
The NIST Cybersecurity Framework 2.0: Using the framework
The framework’s mechanism for describing an organisation’s current or target cybersecurity posture in terms of the Core’s outcomes is called a Framework Profile (Profile).
A "Profile" is a representation of an organisation's cybersecurity outcomes based on its business needs and risk tolerance. Profiles are used to identify the current state of cybersecurity practices and the desired state, which helps organisations prioritise their actions and investments to improve cybersecurity.
The Current Profile represent the "as-is" cybersecurity activities, outcomes, and practices that are currently implemented by an organisation. It provides a clear snapshot of the current cybersecurity posture of the organisation.
The Target Profile represents the "to-be" state, outlining the organisation's desired cybersecurity outcomes. It's based on business needs, risk tolerance, and resources. The Target Profile can be used to identify gaps between the current state and the desired state.
Organisations can start by selecting categories and subcategories from the CSF Core that are relevant to their business context, risk appetite, and cybersecurity requirements. They then align these categories and subcategories with their current cybersecurity practices to create the Current Profile. Next, they determine the desired outcomes and practices to create the Target Profile.
By comparing the Current Profile with the Target Profile, organisations can identify gaps and prioritise areas that need improvement. In addition, Profiles can be used as a communication tool to discuss cybersecurity posture and goals with internal and external stakeholders. Nevertheless, by understanding the gaps between the Current and Target Profiles, organisations can allocate resources more effectively.
Profiles are flexible and can be customised to fit the unique needs, risks, and priorities of each organisation. They can be industry-specific, align with other standards and best practices, or be tailored to address specific threats and vulnerabilities.
In essence, Profiles in the NIST CSF provide a roadmap for organisations to move from their current cybersecurity posture to a more robust and resilient state, aligned with their business objectives and risk tolerance.
A Community Profile is a Target Profile created to address shared interests and goals among a group of organisations. Organisations can consider using it as the basis for their own Target Profile. An example of a CSF 1.1 Community Profile is the NISTIR 8374 Ransomware Risk Management: A Cybersecurity Framework Profile published in February 2022. This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support the identification, protection against, detection, response to, and recovery from ransomware events. The profile serves as a guide for managing the risk of ransomware events, helping organisations assess their readiness to counter ransomware threats and handle potential consequences focusing on 69 subcategories of the total 108. More examples of CSF 1.1 Community Profiles can be found on the NIST Cybersecurity Framework website, which NIST will update as new Community Profiles that are developed for CSF 2.0.
The NIST Cybersecurity Framework 2.0: CSF 2.0 Reference Tool
An online tool is available on the NIST CSF website to showcase the relationships between the Core and Informative References and Implementation examples. This tool, named NIST Cybersecurity Framework (CSF) 2.0 Reference Tool, allows users to explore the Draft CSF 2.0 Core (Functions, Categories, Subcategories, Implementation Examples). The Tool offers human and machine-readable versions of the draft Core (in JSON and Excel). Informative References will be added once CSF 2.0 is finalised in early 2024, which will help to show the connection between the CSF and other cybersecurity frameworks, standards, guidelines, and resources. Since CSF 2.0 Implementation Examples and Informative References will be updated more frequently than the rest of the Core, they will be published and maintained online only.
Click image to view details
The NIST Cybersecurity Framework 2.0: Final remarks
In conclusion, CSF 2.0 seems to be emphasising the importance of top-down governance and the integration of cybersecurity into overall business strategy.
By adding GOVERN function, NIST appears to be addressing the need for a holistic approach to cybersecurity, one that embeds it into the very fabric of organisational strategy and governance. It's a recognition that in today's interconnected digital world, cybersecurity is not just a technical challenge but a strategic imperative.
Ultimately, the evolution of the NIST Cybersecurity Framework from version 1.1 to 2.0, as evidenced by the shift from IDENTIFY to GOVERN, demonstrates the dynamic nature of cybersecurity and the need for frameworks to adapt to changing realities and feedback. It shows the intent to provide organisations with a tool that remains relevant and effective in managing and mitigating cybersecurity risks.