Gaining a better understanding of your cloud applications' attack surface
Properly assessing the security of a cloud application goes beyond using automated tools to discovered misconfigurations. Here’s our comprehensive approach to assessing cloud applications and environments.

Written by:
TL;DR
This blog post discusses how mnemonic’s view of cloud security has developed for several years, and describes our comprehensive methodology for assessing the security of cloud applications and environments. The approach, which has been refined continuously since 2018, has helped customers better understand their attack surface, and has facilitated for structured testing independent of the cloud provider used by the customer.
For customers with a lower budget, our methodology has also helped prioritise their efforts towards the most critical areas of their applications and environments, rather than scattering their efforts across areas with a limited security benefit.
The goal of this article is to raise awareness about the importance of testing cloud applications properly, and help organisations understand the complexity of the attack surface present in their environments.
Organisations with a cloud infrastructure should review whether the attack surface of their application(s) is covered properly, and ensure that they don’t limit their cloud security assessments to misconfigurations discovered with the help of automated tools.
Introduction
Although not fundamentally different from traditional on-premise infrastructure, understanding the complexity of the attack surface present in cloud environments is not always obvious. Misconfigurations are often dubbed as “the new cloud vulnerability”, which many organisations misinterpret as the sole enabling or disabling of a cloud feature.
This belief is amplified due to the popularity of automated configuration-scanning tools and the “quick win” they provide. As a result, many organisations channel most of their resources to addressing isolated misconfigurations, often preventing them from identifying deeper systemic issues, related to strategic and architectural aspects of their environment.
mnemonic’s approach to cloud security
In order to figure out a valuable approach to cloud security testing, we need to understand what the attack surface of a cloud environment looks like.
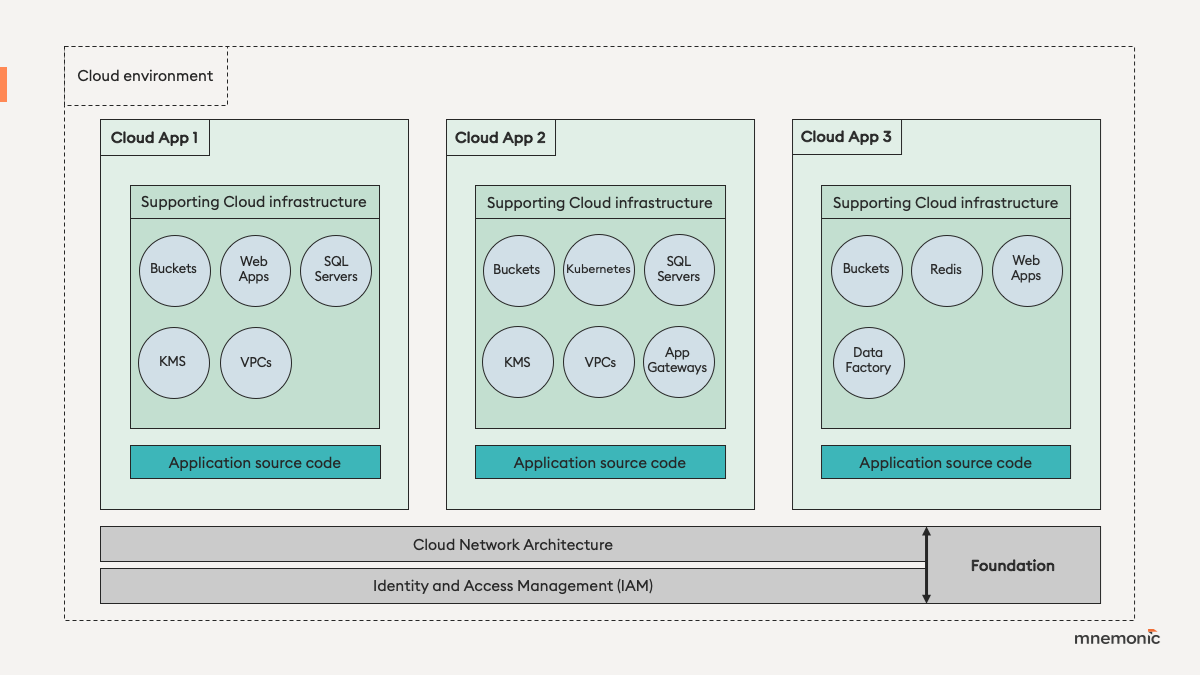
As illustrated in Figure 1, mnemonic divides cloud environments in two main components:
- The foundation of the environment
- Cloud applications
The foundation of the environment is what unifies all of its cloud applications through a shared layer, composed of two distinct areas. First, Identity and Access Management (IAM) is responsible for governing how users, groups and applications are created and access different cloud assets within the environment. Secondly, the environment’s network architecture defines the ability to control, log and monitor traffic across all cloud applications. Therefore, the foundation of the environment affects the security of all its cloud applications, due to the shared and inherent aspect of that fundament.
To build a cloud application you need source code in combination with supporting cloud infrastructure. A cloud environment typically hosts one or multiple “cloud apps”, depending on its purpose within an organisation. Each cloud app can vary in size and architecture, but is typically served to customers in the form of APIs, usually via a frontend client (web, mobile, native client, etc.).
In order to secure a cloud application properly, one needs to start with the shared foundation of the environment, before pursuing its individual components. It is important to note that, ultimately, a cloud application cannot be secured without securing the foundation of its environment first. For example, securing the source code of an application through code reviews and security testing provides no value, if threat actors can easily take over sensitive cloud administrator accounts, and in turn, the entire cloud environment which the application is running in (i.e. failing at securing IAM). Similarly, restricting network access to resources belonging to a single cloud application does not guarantee that it will be the case for other cloud apps, if no proper architecture is in place to control traffic at scale.
mnemonic's methodology for cloud security assessments
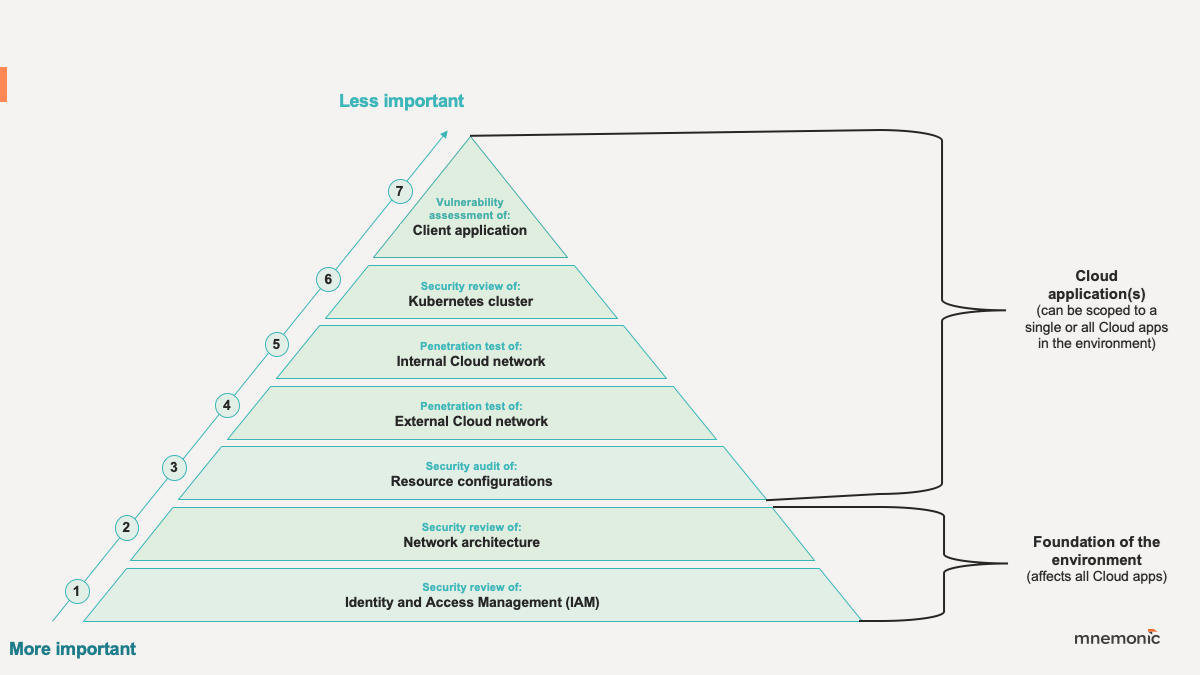
Based on this view of cloud security, mnemonic has developed its own methodology for conducting security assessments of cloud applications, as illustrated in Figure 2. Our methodology is based on the following activities:
Testing the foundation of the environment
1. Security review of: Identity and Access Management (IAM)
2. Security review of: cloud network architecture
Testing cloud applications
3. Security audit of: Resource configurations
4. Penetration test of: External cloud network
5. Penetration test of: Internal cloud network
6. Security review of: Kubernetes cluster (if applicable)
7. Vulnerability assessment of: Client application (web, mobile, native, etc.)
Note that although this blog post is not meant to discuss the differences between a security review, a security audit, a penetration test and a vulnerability assessment in details, they can be concisely summarised as follows:
| Short description | Automated/manual | |
| Security review | Manual review of a complex asset for architectural and strategic issues, as well as advanced attack paths | Little to no automation due to the context-specific aspect of the asset |
| Security audit | Automated scan, output is processed by a consultant for triage, to minimise false positives | Heavily automated |
| Vulnerability assessment | Technical security testing of an asset, with the goal of identifying as many vulnerabilities as possible. Vulnerabilities are confirmed, but exploitation is limited and not systematically applicable (focus on breadth rather than depth) | Partly automated |
| Penetration test | Extension of a vulnerability assessment, goal is to determine the impact of a specific threat scenario. Identified vulnerabilities are exploited to provide access to new attack surfaces, aiming to get deeper into a system (focus on depth rather than breadth) | Partly automated, manual exploitation |
Testing the foundation of a cloud environment
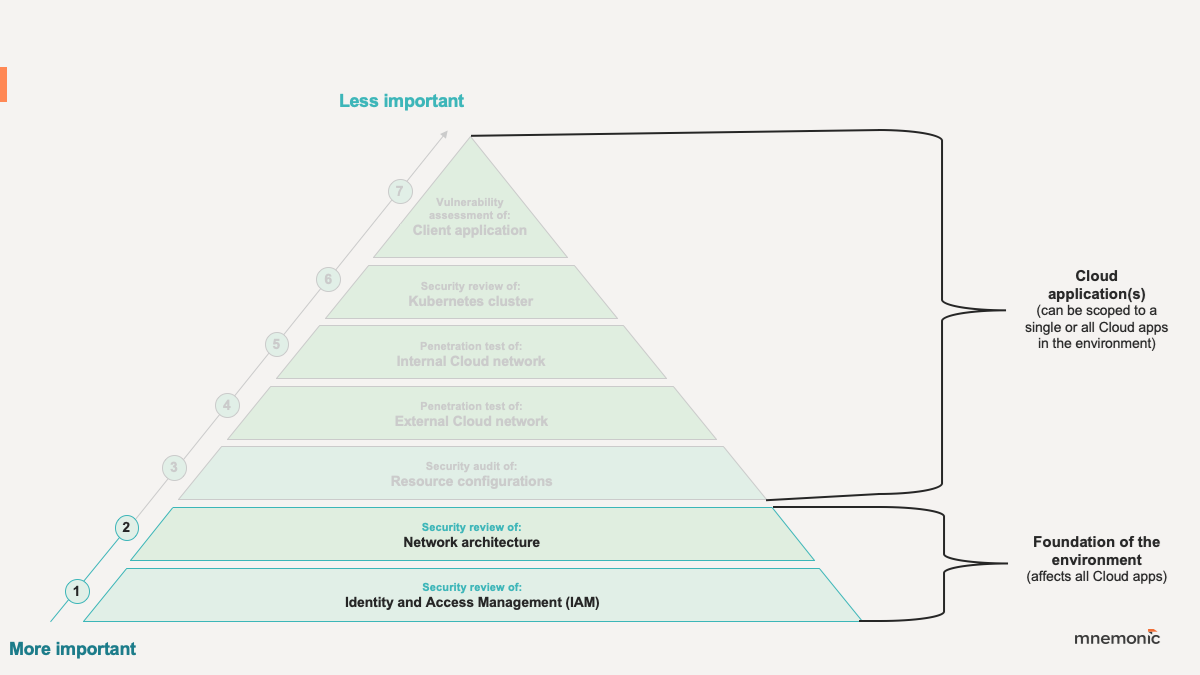
mnemonic tests the foundation of a cloud environment by conducting two main activities:
1. Security review of: Identity and Access Management (IAM)
2. Security review of: cloud network architecture
Security review of: Identity and Access Management (IAM)
The first activity focuses on IAM, as it consists of the most sensitive area of a cloud environment. mnemonic uses a combination of manual testing and automated tools, however this activity consists largely of a manual process. Security testing tools are used to identify basic IAM misconfigurations, which usually embody deviations from mnemonic’s recommended security best practices for IAM. Furthermore, we go on to analyse multiple areas of cloud IAM manually, to identify broader issues related to insecure strategies and practices, as well as advanced attack paths for privilege escalation, typically leading to Global Administrator and tenant takeover. mnemonic uses its own internal methodology to correlate different parts of the cloud IAM configuration, to go beyond simple misconfigurations and identify strategic and structural security issues, which affect all cloud applications and identities within the environment.
Security review of: cloud network architecture
The second activity focuses on reviewing the environment’s network architecture, across all cloud applications. The goal of the activity is to provide a technical quality assurance of the environment’s network topology, and identify architectural issues that may provide an insecure network foundation, create scalability issues or technical debt in the future. For this activity, mnemonic also uses a combination of manual testing and automated tools, although it is still largely a manual process. Automated tooling is used to gather network configuration, while the manual process correlates key information and builds a visual representation of the implemented cloud network architecture. In cases where the customer provides network diagrams, mnemonic also compares the implemented architecture with the documented topology, with the aim of highlighting and visualising any differences between the two.
Testing cloud applications
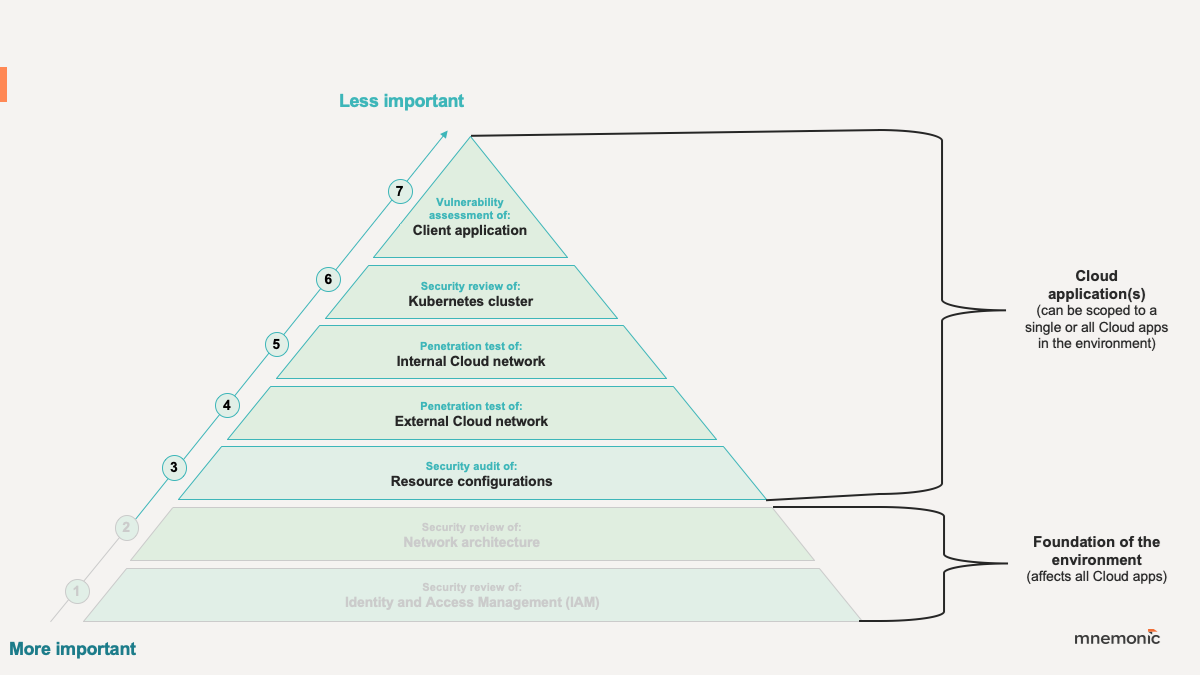
Once the shared foundation of the environment has been tested, mnemonic conducts the following activities to assess the remaining attack surface of each cloud application in scope:
3. Security audit of: Resource configurations
4. Penetration test of: External cloud network
5. Penetration test of: Internal cloud network
6. Security review of: Kubernetes cluster (if applicable)
7. Vulnerability assessment of: Client application (web, mobile, native, etc.)
Security audit of: Resource configurations
Step 3 is where most organisations tend to channel all their efforts. This activity focuses on identifying as many basic misconfigurations as possible in all cloud resources supporting the application. In our methodology, the activity also includes reviewing logging and secret-management practices, something which is considered as extremely sensitive areas, due to their often critical impact (i.e. insecure secret management may establish systemic privilege escalations, while insufficient logging may prevent tracing back a security incident with consequent financial losses). mnemonic uses a combination of manual testing and automated tools, but this activity consists largely of an automated process. Security testing tools are used for automated scanning of cloud resource misconfigurations and help increasing the audit’s coverage. Thereafter, mnemonic consultants conduct a manual verification and analysis of all potential findings to increase the accuracy of reported findings. mnemonic audits the configuration of cloud resources based on security best practices from CIS Foundational Cloud Security Benchmarks, vendor-specific benchmarks and security controls, as well as mnemonic’s own best practices for cloud security.
Penetration test of: External cloud network
The fourth step focuses on mapping out the external attack surface of all cloud resources supporting the application. We identify and analyse any exposed resources to determine their level of exposure and their potential security risk. The first goal of this activity is to give our customer an overview of the cloud services that are exposed to the Internet and identify any external attack surface that may be unknown or uncompliant with centralised cloud network architectures, such as hub-and-spoke topologies. Note that contrary to beliefs observed in some organisations, mapping out the external exposure of a cloud-native application extends well beyond enumerating public IP addresses associated with virtual machines. mnemonic uses a cloud user with full read access to all resources belonging to the cloud application, in order to determine its external attack surface.
The second goal of the activity consists of simulating a threat actor on the Internet without valid access to the cloud application, but with acquired knowledge about the latter’s external attack surface. The threat actor tries to discover and exploit cloud misconfiguration and application vulnerabilities, evade security logic, and cause public-facing services to behave unexpectedly. mnemonic uses a combination of manual testing and automated tools, but this sub-activity consists largely of an automated process. Automated tooling is used to identify the external attack surface of the cloud environment, while a manual process is undertaken to verify the effective exposure and associated risk of potentially exposed resources. The external and unauthenticated attack simulation is carried out using automated web application and infrastructure scanning tools (if applicable), combined with manual testing to go further in depth. Manual testing and analysis ensure that all preliminary results are validated, while enabling mnemonic to look for vulnerabilities and cloud misconfiguration that cannot be tested fully in an automated fashion. Note that mnemonic does not conduct pure volumetric Distributed Denial of Service (DDoS) attacks during this activity, as those do not comply with the security testing policies of most cloud providers.
Penetration test of: Internal cloud network
The fifth activity of our methodology focuses on exploring the possible consequences of a compromised host in one or multiple network locations of the cloud application’s infrastructure. The goal is to test the ability of private cloud networks to limit further attacks leading to privilege escalations and network pivoting, while assessing the efficiency of configured firewall rules. mnemonic conducts penetration tests of internal cloud networks, using either a black-box or white-box approach, although the latter is strongly recommended for most value. Regardless of the approach, mnemonic uses a combination of manual testing and automated tools, but this activity consists largely of a manual process. Security testing tools are used for automated scanning and enumeration, while any step involving the assessment and exploitation of a potential security issue is conducted manually, based on context and other constrains specific to the customer and cloud application. Similar to the previous activity, mnemonic does not conduct pure volumetric DDoS attacks during this activity, in order to comply with the testing policies of most cloud providers.
Security review of: Kubernetes cluster
The sixth step applies for cloud applications based on micro services orchestrated by Kubernetes. When applicable, the goal of this activity is to identify insecure practices, strategies and misconfigurations, which may allow internal and/or external threat actors to bypass authentication and authorisation mechanisms, or escalate privileges within the cluster. Note that due to the integration of managed Kubernetes clusters with the cloud platforms, certain aspects of this activity may be closely-related to other activities, such as IAM, cloud network architecture and testing of external/internal cloud networks. mnemonic uses a combination of manual testing and automated tools, but this activity consists largely of a manual process. Security testing tools are used to identify basic misconfigurations, which usually consist of simple deviations from mnemonic’s recommended security best practices for Kubernetes. The rest of the review consists of analysing multiple areas of the cluster manually, to identify broader issues related to insecure strategies and practices, as well as advanced attack paths for privilege escalations, typically leading to cluster takeover and/or pivoting back to the rest of the cloud infrastructure. mnemonic uses its own internal methodology to correlate different parts of the Kubernetes configuration, to go beyond simple misconfigurations and identify strategic and structural security issues within the cluster.
Vulnerability assessment of: Client application
The seventh and final step to cover the main attack surface of a cloud application focuses on testing the source code of the application. The goal of the activity is to look broadly for logical issues and technical software vulnerabilities, such as those listed in the OWASP Top 10 Web Application Security Risks or similar, depending on the application’s frontend client, if any. During this activity, mnemonic simulates a threat actor using the customer-facing part of the application, typically in the form of APIs with a frontend client (web, mobile, native client, etc.). mnemonic uses a combination of manual testing and automated tools, but this activity consists largely of a manual process. Automated tools are used to get as high coverage as possible, combined with manual analysis to cover “suspicious” areas in greater depth and eliminate false positives. mnemonic typically conducts vulnerability assessments of the customer-facing part of the cloud application using a black-box approach, but white-box testing with access to the source code is preferable for added value.
Feedback from the industry
mnemonic started conducting security assessments of cloud environments as early as 2018. The first years of testing were conducted as general security reviews, using the Microsoft Azure Foundations Benchmark as the main baseline, initially released earlier the same year by the Center of Internet Security (CIS).
Addressing deeper systemic issues
As the cloud industry developed and the need for security assessments increased, mnemonic’s experience and view on cloud security matured in parallel. In early 2021, our team of penetration testers started noticing that the output from security assessments based on CIS benchmarks had a tendency to overly focus on isolated misconfigurations, preventing organisations from addressing deeper systemic issues related to strategic and architectural aspects of their cloud applications and environments. The same kinds of findings kept showing up during re-tests and recurring assessments. However, none of those issues originated from legacy components or unfixable technical debts, like those commonly discovered in on-premises environments with a significantly longer history. Taking good note of that experience, mnemonic started structuring security assessments differently in mid-2021. We started to channel our security reviews towards the most central areas of cloud applications, which we ultimately labelled “the foundation” of a cloud environment, namely:
1. Identity and Access Management (IAM)
2. Cloud network architecture
Besides testing client applications and reviewing cloud resources for basic misconfigurations, the added value from reviewing those areas started to show clearly during recurring assessments and in customer feedback. Security issues that seemed persistent had finally been addressed at the core. This did not mean that new issues of the same kind did not re-appear, but rather than originating from systemic matters they often related to deviations from implemented strategies and architectures. Note that the popularity of policy-driven deployments has significantly helped resolving deviations of this kind in the past few years, although this is out of topic for this blog post.
Understanding the attack surface of cloud applications earlier
mnemonic's security assessments of cloud applications and environments was offered as “general security reviews” until the end of 2022. Although the value of these assessments was undeniable throughout 2022, many organisations still struggled to understand and visualise the structure and attack surface of their cloud applications. Consequently, this made it challenging for mnemonic to describe the value of these new types of assessments, compared to traditional reviews focusing on misconfigurations discovered with the help of automated tools. Although doubtful customers were always convinced after the conduction of an assessment, mnemonic wanted to help organisations understand the attack surface of their cloud applications as early as possible, while providing a structured model to prioritise security-testing activities and efforts.
In January 2023, mnemonic decided to solidify its view on cloud security and formally standardise its way of conducting cloud security assessments to a version similar to what is presented in this article. Throughout the past year, mnemonic has systematically used its new methodology as a starting point to assess cloud applications and environments.
As with any security assessment, the activities effectively conducted have always been adapted to customer maturity, as well as the size and complexity of their cloud applications. Additionally, the presented model does not include the entire attack surface of cloud applications, as the security of deployment pipelines and software development practices are also crucial aspects to consider.
The methodology has facilitated for structured testing activities independent of the cloud provider used by the customer (note that Microsoft Azure is the main provider in Norway), while helping customers better understand the attack surface of their cloud applications. For customers with a lower budget, our methodology has also helped prioritise their efforts towards the most critical areas of their applications and environments, rather than scattering their efforts across areas with a limited security benefit.
Timeline
- 2010: First Azure release
- 2015: Introduction of Azure Resource Manager (ARM) deployments
- 2018: Initial release of CIS Microsoft Azure Foundations Benchmark (version 1.0.0)
- 2018-2020: Early cloud security assessments based on CIS benchmarks
- 2021-2022: Matured cloud security assessments focusing on core areas to address deep systemic issues (still offered as “general security reviews”)
- 2023: Formally standardised methodology for conducting cloud security assessments in January
Concluding remarks
Understanding the complexity of the attack surface present in cloud environments can be a real challenge for many companies, making it hard to structure and prioritise security testing activities. Hopefully, this blog post will help visualise this complexity, and help companies understand the importance of conducting a set of structured security activities, to assess cloud applications comprehensively, beyond basic misconfigurations.
As stated in the very beginning of this blog post, we hope our methodology will inspire others in the world of security to take part in this and set a new standard for the assessment of cloud applications.
For more information, please visit this page describing our cloud security assessment services.