How can a good understanding of threats enable better risk-based security management?
Companies that want to take a risk-based approach to security need a good understanding of threats. Decision-makers can then better prioritise resources for specific and targeted measures adapted to the threats the company faces.

Written by:

TL;DR
A risk-based approach to security management depends on a good understanding of threats. For most companies, it involves understanding the specific tactics and techniques that can exploit vulnerabilities to harm assets. This insight provides a basis for decision-makers to prioritise the security measures best suited to the actual threats the organisation faces. Security measures rooted in an understanding of threats contribute to better resource allocation in preventive security work. A threat assessment is a good place to start.
A good understanding of threats is fundamental for successful security management
In May 2023, the Norwegian National Security Authority (NSM) published a report advising the Norwegian government on a wide range of security challenges, trends, and objectives that should be addressed before 2030. The report is an important contribution to the public debate, and to policy formulation in light of geopolitical volatility and an increasingly complex security landscape. This blog post concerns a fundamental point in the report: the ability to understand threats is a cornerstone of how businesses' work with risk and security management.
“Access to relevant threat and security information is crucial for companies' work with security and for regular updating of risk assessments. Updated threat and security information can change the premises for the current risk assessment, thus requiring a new evaluation with new measures.”
NSM, 2023 (unofficial translation)
Understand the threat landscape to prioritise the right security measures
A good understanding of your business’ threat landscape is a necessary prerequisite for implementing well-considered security measures based on risk. Threat intelligence is a crucial input to risk assessments and how the company works with security. We must understand the threat landscape to make informed choices about protective measures, and threat intelligence should be an integral part of risk and security management in companies and governmental entities.
It is necessary to understand the strategic and geopolitical context we find ourselves in. The government's publicly available information about vulnerable sectors and the threat actors' objectives is a starting point. But it is not enough. The publicly available security and threat assessments produced by many Western governments set an important strategic framework but can be difficult to translate into concrete security measures for individual companies. The underlying information and data are often classified, and have a legitimate need for confidentiality. Access to classified information wouldn’t necessarily be an adequate solution. The mandates and mission-focus of the intelligence and security services overlap only to a limited extent with the information needs of most private and public companies.
It is "typically Norwegian to be good... at describing the situation," Øyvind Husby, CEO of ICT-Norway stated earlier this year (authors own translation). Situational awareness, to understand the situation, in itself does not provide protection. However, it does provide an informed basis for action. We must have knowledge of the specific tactics and techniques an attacker can use against us in order to choose the most appropriate countermeasures. We need a fact-based information basis to assess which threats can exploit our vulnerabilities to harm our assets.
For many companies it will be inefficient to focus on attribution, that is, who is behind an attack or poses a threat. The threat landscape is constantly evolving, and attribution is technically difficult. In addition, tactics and techniques are used across different actors and categories of actors, such as state intelligence services and professional criminal groups.
Of course, attribution can be very important to the authorities. For example, if military plans or political decision-making processes lose confidentiality it is relevant to know who got hold of the material. Another example would be sabotage and destructive cyber operations, where credible attribution could be crucial to ensure a coherent allied response. However, for most Norwegian companies, attribution is not necessary to assess what are the relevant security measures to detect, prevent, and respond to unwanted activity. What they need is concrete and detailed information about the means an attacker can use to harm them. Attribution can still be valuable in the investigation of serious incidents, but this usually requires involvement from specialised forensics capabilities.
Resilient organisations work holistically and continuously with security management
“Risk assessments and security measures must change more frequently in line with a constantly changing risk landscape.”
Norwegian Defence Commission (NOU 2023:14) (unofficial translation)
Knowledge about threats is a cornerstone in proactive and continuous work with security management. This requires robust organisations capable of working cross-functionally with risk, threat intelligence, and technical solutions. One approach is to describe scenarios, expressed as specific threat events, that the company can be exposed to. The scenarios provide an informed basis for developing protective measures and security solutions. In this way, a risk-based and holistic approach to security can be built layer by layer.
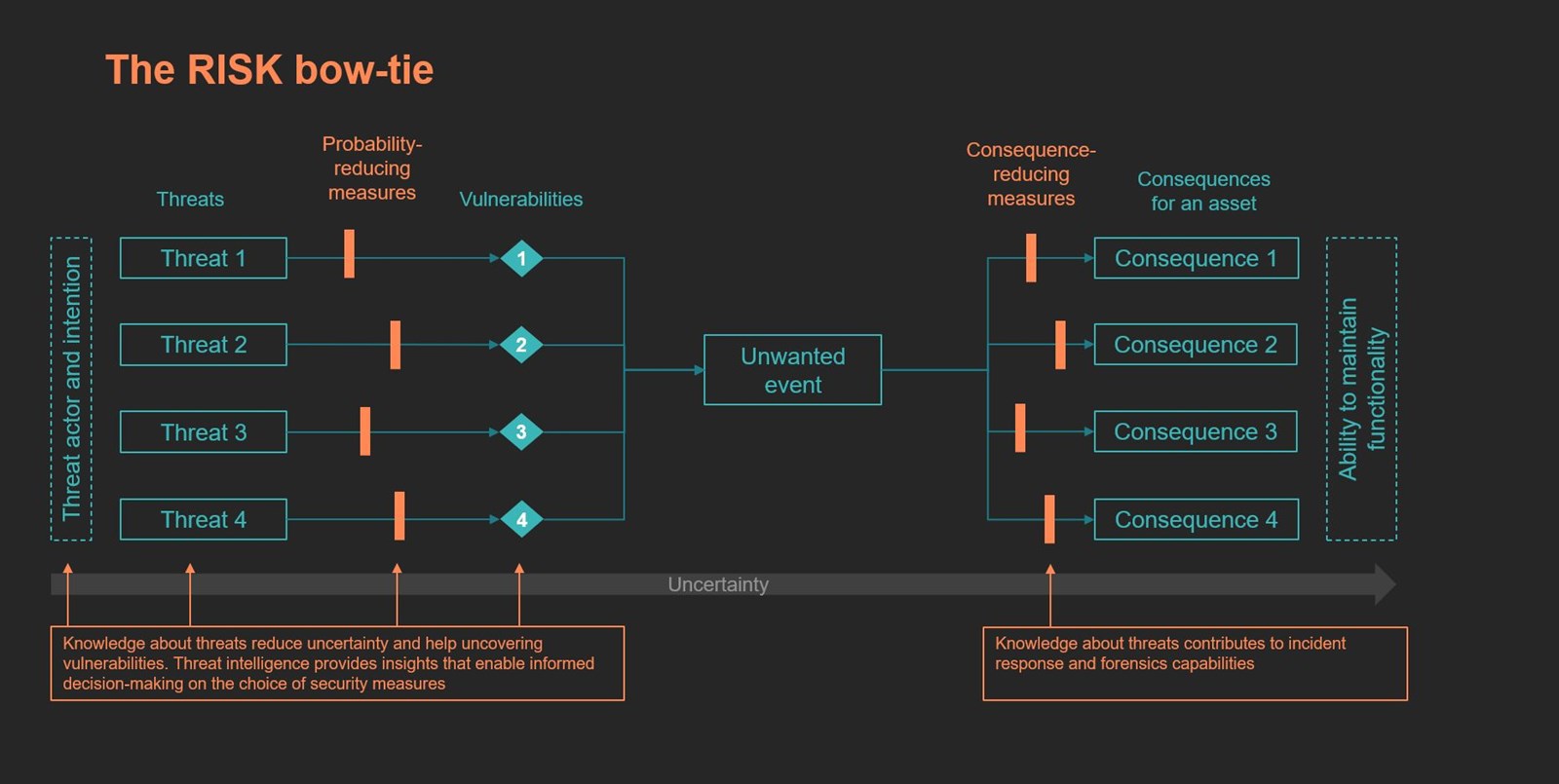
Standards Norway uses a bow-tie model to visualise risk (NS 5814:2021). The model can be used to visualise the relationship between threats, vulnerabilities, and assets in risk management. Knowledge and understanding of threats are important throughout the bow-tie model of risk, for example when it comes to detection, the choice of security measures and incident handling.
Ask the right questions about the threats facing your organisation
Senior management is responsible for defining the organisation's risk tolerance. Therefore, the risk the organisation faces is an important information requirement. For the security organisation to meet this requirement, it's crucial that they specify and manage information requirements about the threat landscape through a structured process (Information Requirement Management). A threat assessment is an important input to the risk assessment, and the risk assessment provide a basis for developing new information requirements about threats. In effect, this process helps the whole organisation understand their threat landscape better, enabling better risk management.
Leadership engagement ensures that the work with threat intelligence is linked to the company's long-term security work and is anchored in the company's security and business objectives. In this way, information requirement management becomes a part of the overall risk and security management process.
Concluding remarks: knowledge about threats contribute to a good security baseline
A hardening geopolitical climate, an evolving threat landscape and rapid technological developments require continuous work with security. Governments and private actors must work together, while simultaneously having a good understanding of their roles. The authorities help to explain the overall geopolitical developments and strategic threat landscape. The formulation and enforcement of laws and regulations are critically important to ensure security across sectors and defend one’s international competitiveness. In Norway, the Ministries are tasked with defining so-called “fundamental national functions (GNF)” in line with the Security Act. There is also a proposed new law on digital security, aligned with EU regulations (NIS directive). These are examples of important ongoing government-led processes that affect businesses.
At the same time, it is the responsibility of every individual company to ensure that they have an adequate security baseline. Hence, companies must plan and prepare for additional security measures in case there is a change in the threat landscape. This requires a holistic and risk-based security management system, as well as measures that are adapted to the actual threat the company faces.
| Threat | “An intentional action that can lead to an unwanted event” (NS 5814:2021). Unofficial translation. |
| Vulnerability |
“Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source” (NIST). The relationship between threats and vulnerabilities is complex and seldom one-to-one. A vulnerability can potentially be exploited by multiple threats, and a threat can potentially exploit multiple vulnerabilities. The hunt for vulnerabilities can be made proactive through measures such as continuous vulnerability scanning. |
| Probability-reducing measures | Security measures intended to prevent, detect, delay, or stop a threat (NS 5814:2021). Also referred to as control measures. The purpose is to reduce the room available for exploiting vulnerabilities. Knowledge about specific threats provides a better basis for decision-making in selecting the right measures. Control measures and technical security solutions should be linked to specific threats and evaluated scenarios (unwanted/threat events). An example of how this can be done is mnemonic’s Enterprise Security Architecture framework. |
| Unwanted event | "An event that can expose an asset to unwanted influence" (NS 5830:2012). Here understood as a scenario. The level of detail is adjusted as needed. |
| Consequence reducing measures | Security measures that are meant to reduce the effect of an event, for example by responding, limiting and resuming/recovering (NS 5814:2021). Knowledge about threats can contribute to the right measures being taken, and faster decision-making processes. Threat intelligence can be integrated into the routines for incident response. |
| Consequences for an asset | An unwanted event can have multiple consequences for a company's assets. |
| Uncertainty | Uncertainty is fundamental to address when working with risk and security. Even though uncertainty can be reduced through threat intelligence and good decision-making processes, there will always be uncertainty. This uncertainty must be communicated to, and understood by, senior management. |
Get in touch